Buy Courses & Training
Showing 17–32 of 55 results
-
K0680 Cybersecurity principles and practices
Cyber security starts with a risk-based approach that father was a good system security engineering path. it includes business operations and technical processes that will enforce the organizations risk stance.
Original price was: $15.00.$8.00Current price is: $8.00. -
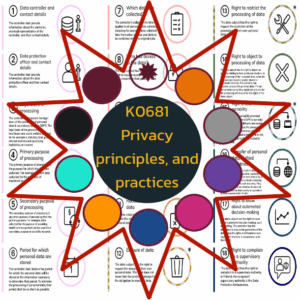
K0681 Privacy principles and practices
In order to protect the privacy of individuals that interact with our organization, we must do a recurring privacy impact assessment. This includes: technical, operational, business, and lifecycle processes to be adjusted away from what is good for the organization and toward what is good for the individual.
Original price was: $15.00.$8.00Current price is: $8.00. -
K0682 Cybersecurity threats
The methodology for consuming threat data and building threat models requires an understanding of adversarial activities defined in a structured way. This structure will help us to calculate weaknesses in the context of our organization.
Original price was: $15.00.$8.00Current price is: $8.00. -
K0684 Cybersecurity threat characteristics
Once you have reviewed the free threats and vulnerabilities introduction the deep detail of AT&CK and CAPEC will make sense. The proactive and reactive controls that match up to these major methodologies will ensure the success of the enterprise in reducing threats based on their characteristics.
Original price was: $15.00.$8.00Current price is: $8.00. -
K0686 Authentication and Authorization tools and techniques
Authentication and authorization must be based upon core engineering principles of choosing the right access control system. Only then will the standards governance and risk be addressed within our organization. Choosing the wrong access control methodology is like using a hammer to drive a screw. Must also considerTechnical operational business
Read moreOriginal price was: $15.00.$8.00Current price is: $8.00. -
K0692 Vulnerability assessment tools and techniques
Vulnerability assessment is both a technical inventory and the business metrics to communicate that technical in inventory. The process includes: asset information, scanning, verifying results, and updating configuration management data.
Original price was: $15.00.$8.00Current price is: $8.00. -
K0697 Encryption algorithm capabilities and applications
Encryption algorithm capabilities must be matched to the business need. This requires an understanding of the operations and technical processes as well as the lifecycle of all encryption, algorithms deployed in the environment.
Original price was: $15.00.$8.00Current price is: $8.00. -
K0698 Cryptographic Key Management principles and practices
Deploying public key infrastructure and certificate authorities requires a clear understanding of business and operations processes along with the technical aspects of certificate lifecycle.
Original price was: $15.00.$8.00Current price is: $8.00. -
K0709 Business Continuity and Disaster Recovery policies and procedures
The seven phases of business continuity planning will build resiliency and redundancy across all technology assets protecting mission data. There are four major standards for business continuity planning that are accepted, globally. The three major components of the methodology include the business process analysis, business impact analysis, and finally the
Read moreOriginal price was: $15.00.$8.00Current price is: $8.00. -
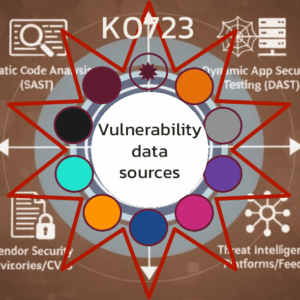
K0723 Vulnerability Data Sources
In order to understand CVE & NVD we must go deeper into vendor databases, open source information, and data analysis for prioritizing the consumption of vulnerability data sources.
Original price was: $15.00.$8.00Current price is: $8.00. -
K0728 Confidentiality, Integrity and Availability principles and practices
The heart of every CyberSecurity program requires four terms be well understood and applied by everyone in the organization. You could only do one course in cyber security this course will do the most good for the most people.
Original price was: $15.00.$8.00Current price is: $8.00. -
K0751 System Threats
Understand how to build a threat model and perform a business impact analysis. Governance requires that you understand the basis for analysis and the potential consequences of not addressing system threats from a compliance standpoint. A business impact analysis is critical for the long-term survivability of an organization and it’s
Read moreOriginal price was: $15.00.$8.00Current price is: $8.00. -
K0752 System Vulnerabilities
Vulnerabilities include: external resources, supply chain, and internally built software. Knowing how to organize the vulnerabilities and calculate a base score requires a clear understanding of the scoring system, business processes, and how this integrates with change control.
Original price was: $15.00.$8.00Current price is: $8.00. -
K0785 Insider threat tools and techniques
Employees, contractors, vendors are considered insiders. They have a different set up protections under the law. These are special set of threat agents that can have devastating impact if we do not deploy governance, methodologies, and policies in a clear correct manner. We must also look for the technical indicatorsOf
Read moreOriginal price was: $15.00.$8.00Current price is: $8.00. -
K0798 Program Management principles and practices
The technological and business process of program management requires a firm understanding of the three levels of systems, assets, and their delivery protocols.
Original price was: $15.00.$8.00Current price is: $8.00. -
K0803 Supply Chain Risk Management principles and practices
Defining the surface area of your supplychain risk management requires: contractual review, system definition, and monitoring across all your operational processes.
Original price was: $15.00.$8.00Current price is: $8.00.